Top Cybersecurity Audit Services 2025 to boost protection and profits with expert risk assessments.
Your board wants proof: that every dollar spent on security creates measurable value—fewer incidents, faster enterprise sales, lower premiums, and confident audits. A well-run cybersecurity audit service does exactly that. It translates technical safeguards into evidence executives trust and buyers sign off on. In Tier One markets (USA, UK, Canada, Australia), procurement teams now gate deals behind security questionnaires, SOC 2/ISO attestations, and sector regulations. Fail the test, and growth stalls. Pass with clarity—and you’ll unlock bigger contracts, smoother renewals, and stronger valuations.
This guide shows how to structure audits for ROI, not just compliance theater. You’ll see mini case studies, comparison tables, and a step-by-step cyber security audit checklist you can deploy today. We’ll also unpack cyber security audit certification paths, discuss providers (including boutique firms and players in niches like Arculus cyber security services), and map audit outputs to marketing assets that shorten security reviews. Promise: by the end, you’ll know which audit to run, when to run it, and how to translate findings into conversion-driving proof for customers, regulators, and insurers. Key Tip: Treat audits as a growth engine—a pipeline of trust signals, not just a cost center.
How Our Cybersecurity Audit Services Help Enterprises Achieve ROI and Trust
Security audits deliver value when they align with revenue levers—customer trust, compliance clearance, and resilience. We structure engagements around your sales cycle and risk register, then baseline controls across identity, endpoints, networks, cloud, applications, and data governance.
Mini Case Study (USA SaaS, Mid-Market): Sales was losing momentum at the security-review stage. We executed a readiness audit mapped to SOC 2/ISO 27001 controls, closed 23 gaps, and packaged evidence into a Trust Center (policy index, pentest summary, architecture diagram). Result: security review cycle time dropped from 5.4 weeks to 2.1 weeks, and quarterly win rate rose 9%.
ROI levers we track
| Lever | Audit Mechanism | Business Result |
| Faster deals | Evidence library + mapped controls | Shorter security questionnaires |
| Lower loss likelihood | Hardening + detections audit | Fewer incidents, better MTTR |
| Insurance readiness | Control attestations + logs | Premium stabilization |
| Tool consolidation | Overlap analysis | Reduced spend & complexity |
Takeaway: Tie each audit objective to a business KPI (time-to-close, MTTR, premium).
Why Cybersecurity Audits Are Essential for Compliance and Growth in Tier One Markets
Regulators and enterprise buyers across the USA, UK, Canada, and Australia expect verifiable controls. Audits transform “we’re secure” into verifiable proof. They also reveal duplicated tools, unsafe defaults, and silent failure modes that drain budgets.
Mini Case Study (UK Fintech): Quarterly internal audit exposed weak access recertification. After remediation (automated JML, quarterly reviews, Just-In-Time admin), a major bank completed due diligence in record time, unlocking a multi-year agreement.
Compliance & growth alignment
| Region | Common Buyer/Reg. Drivers | Audit Focus |
| USA | SOC 2, PCI DSS, HIPAA, insurer questionnaires | Logging, IR playbooks, vendor risk |
| UK | ISO 27001, GDPR, NCSC guidance | Data governance, DPIAs, access control |
| Canada | PIPEDA, sectoral rules, SOC 2 | Privacy-by-design, evidence depth |
| Australia | Privacy Act, Essential Eight | Patch maturity, application control |
Result: Use audits to pre-answer buyer questionnaires.
Key Tip: Publish a security overview PDF so procurement trusts you before the first call.
Comprehensive Cybersecurity Auditing Services for Enterprises and SMBs
We deliver end-to-end audit coverage—from governance to endpoint hardening—so you can pick modular services or a full program.
- GRC/Policy Audit: Framework mapping (NIST CSF/ISO 27001/CIS), risk register health, vendor risk program.
- Technical Control Audit: Identity (SSO/MFA/PAM), endpoint (EDR/BYOD), network (segmentation/NDR), cloud (CSPM/CIEM), AppSec (SAST/DAST/SBOM).
- Operational Resilience: Backup/restore drills, BCP/DR tests, incident tabletop exercises.
- Evidence & Reporting: Control narratives, screenshots, log exports, and remediation roadmaps.
Service snapshot
| Service | Audience | Primary Outcome |
| Readiness Audit | Pre-SOC2/ISO teams | Gap list + evidence plan |
| Cloud Audit | SaaS & fintech | Misconfig kill list, IAM cleanup |
| Network Audit | Hybrid orgs | Segmentation + visibility uplift |
| AppSec Audit | Product orgs | SDLC guardrails + defect trend |
Takeaway: Start with readiness, then run targeted audits quarterly.
Explore more details here → Request our artifact checklist (what we collect, how we store, retention).
What Are the Different Types of Cybersecurity Audit Services Enterprises Should Know?
Different audit types answer different buyer and regulator questions:
- Readiness vs Certification: Readiness prepares; certification verifies (e.g., ISO audits by accredited bodies, SOC 2 by CPA firms).
- Internal vs External: Internal builds muscle; external validates to the market.
- Thematic Audits: Focused slices—Identity, Cloud, Network, AppSec, Data Privacy, OT/ICS.
- Vendor/Supplier Audits: Third-party risk validation (questionnaires, attestations, spot checks).
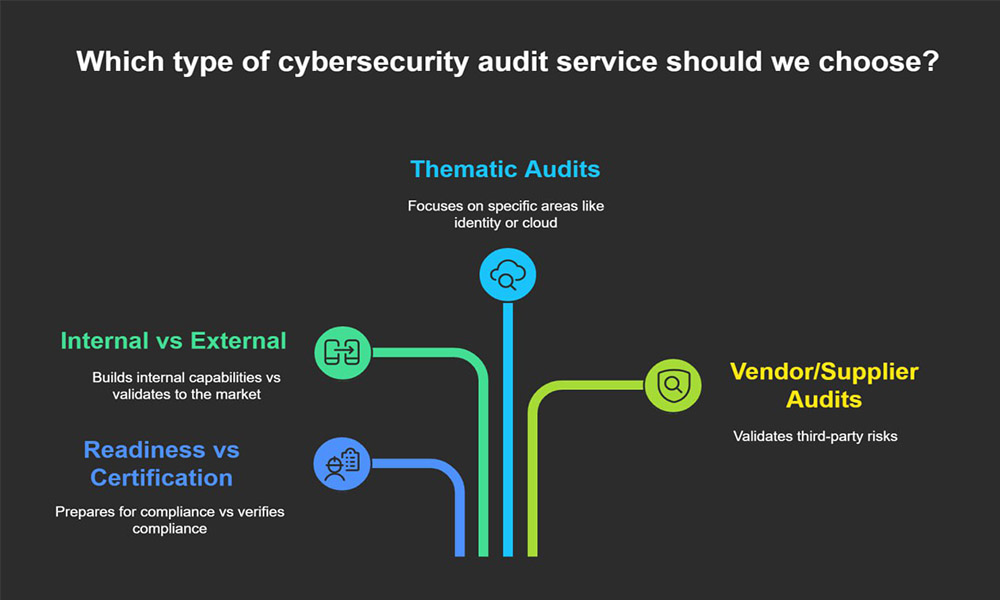
Type comparison
| Type | Best For | Caveat |
| Readiness | New programs | Needs leadership buy-in to fix gaps |
| External | Market trust | Scheduling + cost |
| Thematic | Fast improvements | Must roll up into a program |
| Supplier | Enterprise sales | Requires clear remediation timelines |
Result: Choose thematic audits to show wins fast.
Key Tip: Keep a single control catalog so all audits map to one language.
Challenges Businesses Face Without Cybersecurity Audit Programs in the USA & UK
- Sales drag: Security questionnaires stall deals; missing artifacts trigger long delays.
- Invisible risk: Misconfigurations, weak access controls, and untested recovery stay hidden until a breach.
- Tool sprawl: Overlapping licenses increase cost without lifting controls.
- Insurance pressure: Carriers demand controls; without proof, premiums spike or coverage shrinks.
Impact table
| Gap | Business Effect | Fix via Audit |
| No access recert | Privilege creep | IAM review + JML automation |
| Weak logging | Slow investigations | SIEM data quality audit |
| Patch drift | Exploitable assets | Patch cadence measurement |
| Cloud sprawl | Shadow services | CSPM baseline + tagging policy |
Takeaway: If you can’t evidence a control, auditors assume it doesn’t exist.
Explore more details here → Ask for a 30-control quick scan to triage priorities.
IT System Design and Effectiveness Evaluation for Risk-Free Growth
Audits don’t stop at “is it configured?”—they measure effectiveness. We examine architecture, blast-radius, and failure modes through tabletop scenarios and data-driven tests (e.g., restore speed, alert fidelity).
Pros & cons
| Approach | Pro | Con |
| Design review | Future-proofs architecture | Abstract without tests |
| Live control tests | Proves effectiveness | Needs safe staging |
| Tabletop exercises | Aligns teams | Not a substitute for drills |
Expert Insight: Pair design review with control validation and at least one restore test—that trifecta reveals real risk.
Qualysec Cybersecurity Audit: Building Enterprise Trust and Compliance
Boutique partners like Qualysec specialize in penetration testing and audit support that convert technical findings into board-ready narratives. We often collaborate with boutiques to provide depth in AppSec and scenario testing, then integrate results into your control catalog and evidence library for buyer reviews.
Value mapping
| Capability | Business Outcome |
| AppSec + pentest | Fewer prod defects, better buyer confidence |
| Remediation guidance | Faster closure, cleaner re-tests |
| Evidence packaging | Shorter questionnaires, repeatable audits |
Expert Insight: Ask boutiques to deliver exec summaries + raw artifacts—you’ll need both for sales and engineering.
Network Security Audit Services That Enhance ROI and Data Protection
A network security audit validates segmentation, egress controls, DNS/DHCP hygiene, VPN posture, and logging at choke points. We review firewall rule sets, Zero Trust policies, and NDR visibility to shrink lateral movement.
Scope overview
| Area | What We Check | Why It Matters |
| Segmentation | VLANs/ACLs/East-West | Limits breach blast-radius |
| Perimeter | WAF/IDS/geo/egress | Blocks commodity attacks/data exfil |
| Remote access | MFA/device posture | Stops credential stuffing |
| Telemetry | Syslog/SIEM/NDR | Faster detection & IR |
Expert Insight: Replace “allow any” with least-privilege rules audited quarterly.
Audit Reporting and Recommendations That Drive Conversions and Stakeholder Confidence
Reports must sell clarity: an executive summary that maps risks to revenue impact, a prioritized remediation plan, and an evidence appendix customers and auditors can reuse.
What great reports include
| Section | Contains |
| Exec summary | Top risks, business impact, timeline |
| Roadmap | Sequenced fixes with owners/effort |
| Evidence pack | Screenshots, logs, policies, diagrams |
| Metrics | Before/after risk & control coverage |
Expert Insight: Convert findings into website-ready statements (e.g., “MFA enforced org-wide; quarterly access reviews”) for your Trust Center.
Vulnerability Management Services for Enterprise-Level Risk Mitigation
Audits often uncover scan-to-patch friction. We build a measurable program: authenticated scans, risk-based prioritization, maintenance windows, and SLA tracking to keep patch debt low.
Program building blocks
| Component | Detail |
| Coverage | Authenticated scans (servers, endpoints, cloud) |
| Prioritization | CVSS + exploit intel + asset criticality |
| Execution | Change windows, rollback plans |
| Evidence | Trend reports for auditors/insurers |
Expert Insight: Track “time to remediate exploitable vulns,” not just counts.
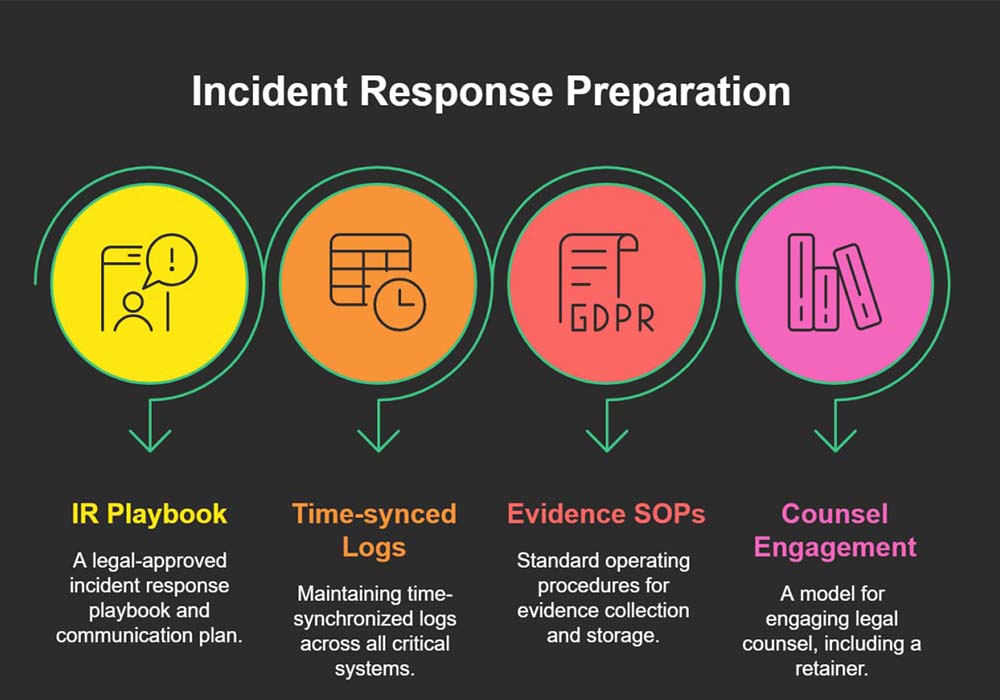
Dovetailing Legal Tech and Forensics into Cybersecurity Audit Processes
Legal and forensics are audit multipliers. We align incident response plans with counsel guidance, litigation holds, and forensic readiness (time-sync, immutable logs, chain of custody). This preserves options if investigations or notifications arise.
Checklist
- Legal-approved IR playbook & comms plan
- Time-synced logs across critical systems
- Evidence collection SOPs and storage
- Counsel engagement model (retainer)
Key Cybersecurity Audit Services Offered by Qualysec for Tier One Enterprises
- External/Internal Pentesting with proof-of-exploit artifacts
- Web/Mobile/API testing aligned with OWASP
- Cloud posture reviews and IaC misconfig assessments
- Secure SDLC advisories and retest cycles
How Physical Security Audits Strengthen Digital Defense ROI
Badges, visitor logs, camera coverage, and server room controls backstop digital safeguards. We validate asset custody, media disposal, and clean desk policies—controls often requested in audits.
Focus points
| Control | Business Link |
| Access logs | Insider risk accountability |
| Media handling | Data lifecycle proof |
| Environmental | Uptime & safety |
Why Choose Our Cybersecurity Audit Services in the USA, UK, Canada & Australia?
- Growth-first framing: Evidence designed to close deals.
- Operator DNA: Cloud/AppSec/IAM engineers who speak auditor & buyer.
- Artifact excellence: Clean, reusable proof packs.
- Partner ecosystem: From boutiques (e.g., Qualysec) to enterprise assessors.
Step-by-Step Guide: Cybersecurity Audit Checklist for Enterprises
- Scope & Framework: Pick NIST CSF/ISO; set audit boundaries.
- Asset & Data Map: Systems, SaaS, integrations, data classes.
- Identity Review: MFA, RBAC, PAM, access recerts.
- Endpoint/Server: Hardening, EDR coverage, patch cadence.
- Network: Segmentation, egress, VPN, DNS security.
- Cloud: IAM policies, encryption, public exposures, backups.
- AppSec: SDLC, SAST/DAST, SBOM, secrets management.
- Logging & SIEM: Sources, retention, correlation, alert SLAs.
- IR & BCP/DR: Playbooks, drills, restore tests, comms.
- Vendor Risk: DPAs, questionnaires, monitoring.
- Evidence Pack: Screenshots, configs, reports.
- Roadmap: Prioritized fixes, owners, target dates.
Latest Penetration Testing Report: Key Insights for Enterprise Decision-Makers
Your pentest should rank findings by exploitability + business impact and include retest guidance. Look for patterns (auth bypass, excessive permissions, missing rate limits). Use results to update SDLC guardrails and buyer-facing assurance statements.
Tiny table
| Pattern | Preventive Control |
| IDOR | Authorization checks, tests |
| Weak auth | MFA, rate limits, risk-based auth |
| Secrets in code | Secrets scanning, vaulting |
Consulting Services That Deliver ROI from Cybersecurity Audits
We transform findings into funded roadmaps: quantify risk, align with contracts/SLAs, and define OKRs. We implement quick wins (MFA coverage, backup tests), then stage higher-effort items (IAM refactor, SDLC uplift). Outcome: control maturity climbs and sales move faster.
Certifications for Executives: Enhancing Governance and Compliance
Executive literacy closes gaps. Popular tracks: CISA, CRISC, CISSP, ISO 27001 Lead Implementer/Auditor. Short courses on NIST CSF and board-level cyber risk help leaders interpret audit outputs and fund the right fixes.
Industry Trend: Growth of Cybersecurity Audit Services in the US and UK Enterprise Sector
Demand is rising as insurers tighten underwriting and enterprises expand third-party risk programs. Add rapid cloud adoption and software supply-chain scrutiny (SBOMs), and audits become continuous—not annual. Smart teams operationalize audits as a rhythm, not a fire drill.
What is a Cybersecurity Audit? Expert Insights from Global Advisors
A structured evaluation of security controls, processes, and evidence against a recognized framework. It verifies design and effectiveness, produces a remediation plan, and packages proof for buyers, regulators, and insurers. Think of it as a quality system for security.
What Are the 7 Types of Cybersecurity and Their Role in Audit Services?
Network, Endpoint, Application, Cloud, Identity & Access, Data Security, and Security Operations/IR. Audits test each domain’s controls and the hand-offs between them (e.g., identity signals driving endpoint posture).
How Much Does a Cybersecurity Audit Cost in the USA, UK, Canada & Australia?
Costs vary by scope, size, evidence depth, and certification plans. Readiness and thematic audits are typically most affordable; full external certifications and broad pentesting programs cost more. The strongest ROI comes from prioritized roadmaps and evidence reuse across audits and buyers.
What is the Role of a Cybersecurity Audit in Enterprise Growth and Trust?
Audits create credible, repeatable proof that reduces buyer friction, stabilizes premiums, and boosts resilience. Use outputs to accelerate enterprise sales, support renewals, and strengthen board confidence in the program.
Gartner & IDC Reports: ROI and Adoption Rates of Cybersecurity Audit Services
Industry analysts consistently note increased adoption of continuous assurance and evidence automation. Programs that map controls to business metrics (e.g., time-to-close deals, MTTR) demonstrate the clearest ROI.
FAQs:
What is included in a cybersecurity audit checklist for enterprises?
Core elements: scope/framework selection; asset/data mapping; identity (MFA, RBAC, PAM); endpoint/server hardening and patching; network segmentation and egress controls; cloud IAM and encryption; AppSec/SDLC with testing; logging/SIEM and alert SLAs; IR/BCP/DR with restore tests; vendor risk; and a documented evidence pack. Finish with a prioritized remediation roadmap tied to business KPIs like time-to-close and MTTR. Takeaway: Evidence + roadmap = trust + action.
Which cybersecurity audit certification is best for ROI in the USA and UK?
Pick the certification your buyers ask for. Commonly, SOC 2 (attestation) for US B2B SaaS and ISO 27001 (certification) for UK/EU/global buyers. Regulated sectors may require PCI DSS (payments) or HIPAA (health). Key Tip: Start with a readiness audit, then pursue the certification that aligns with your pipeline.
How much does a cybersecurity audit cost for small businesses vs enterprises?
Costs scale with asset count, cloud/services breadth, pentest scope, and evidence needs. SMBs often start with readiness + focused pentest; enterprises budget for multiple thematic audits and external assessments. Optimize spend via tool overlap reduction and evidence reuse across customers and certifications.
What is the best cybersecurity audit program for compliance in Tier One markets?
A unified control catalog mapped to NIST CSF/ISO 27001, refreshed quarterly, with targeted audits (Identity, Cloud, AppSec) and an evidence library. Add incident tabletop drills and restore tests. This program accelerates SOC 2/ISO, satisfies buyer questionnaires, and improves resilience.
Cybersecurity audit PDF – where to download free and paid resources?
Look for framework guides (NIST CSF/ISO), checklists, and IR templates from reputable standards bodies and professional associations. Use them to build an internal audit runbook and adapt for buyer questionnaires.
Cybersecurity audit services certification – which providers are trusted globally?
For ISO 27001, select an accredited certification body. For SOC 2, work with experienced CPA firms. For pentesting and thematic audits, partner with reputable boutiques (e.g., firms like Qualysec) and ensure deliverables include exec summaries + raw artifacts.
What is the average cybersecurity auditor salary in the USA, UK, Canada, and Australia?
Compensation varies by region, seniority, sector, and certification stack (e.g., CISA, ISO Lead Auditor). Generally, regulated industries and major metros pay more; leadership roles and hybrid GRC/technical skillsets command premiums. Result: Grow your value by linking audits to measurable business outcomes and mentoring teams.
What are the top cybersecurity audit jobs available for certified professionals?
Roles include IT Auditor (GRC), Cybersecurity Auditor/Assessor, ISO Lead Auditor, SOC 2 Readiness Consultant, PCI QSA team member (with the right affiliation), and Security Program Manager. Technical hybrids span Cloud/Posture Auditor, AppSec Auditor, and IR/BCP Assessor.
Cybersecurity audit services comparison: On-Prem vs Cloud Audit ROI
Cloud audits often deliver faster ROI via centralized IAM, policy as code, and CSPM findings. On-prem audits may require broader physical and network control checks. Best practice: hybrid audits that ensure consistent policies and evidence across both.
Cybersecurity audit services near me – best providers in the USA and UK
Choose providers with sector references, clear deliverables, and placement on accredited registries where applicable. Interview teams for domain depth (cloud/IAM/AppSec), not just checklists. Ask for sample reports and a remediation plan example.
What are the key benefits of cybersecurity audit services for enterprise lead generation?
Audit outputs Power Trust Centers, shorten questionnaires, and add proof points to RFPs (MFA coverage, restore drill cadence, pentest recency). This lifts close rates, renewals, and ACV—direct growth impacts beyond risk reduction.
How to prepare for a cybersecurity audit step-by-step checklist?
(1) Pick framework & scope, (2) inventory systems/data, (3) gather policies/procedures, (4) export identity & logging evidence, (5) validate backups & restores, (6) list third-party apps/vendors, (7) stage proofs (screenshots/logs), (8) pre-run an internal quick audit, (9) assign owners for each control, (10) book stakeholder interviews.
Cybersecurity audit best practices for financial services and healthcare enterprises
Map controls to regulatory obligations (PCI, SOX, HIPAA, GDPR), enforce least privilege, encrypt data, log comprehensively, and test restores. Maintain vendor risk rigor and segregation of duties. Keep evidence current and ready for regulators and buyers.
What is the ROI of cybersecurity audit services for global enterprises?
ROI appears as faster sales, reduced incident frequency/impact, insurance compliance, and tooling efficiencies. Convert findings into executive metrics (time-to-close, MTTR, % MFA coverage, restore RTO). Re-measure after remediation to prove uplift.
Cybersecurity audit consulting services – how they support compliance and conversion
Consultants translate frameworks into doable sprints, coach teams through remediation, and create board-friendly narratives. They also build evidence libraries you can reuse across deals, which compounds value every quarter.
