Compare information security vs cybersecurity for ROI, compliance & careers in USA, UK, Canada & Australia. Roles, salaries & 2025 tips.
You’re deciding between two powerhouse paths—Information Security (InfoSec) and Cybersecurity—and the stakes are real: regulatory risk, brand trust, and seven-figure incident costs when things go wrong. In Tier One markets (USA, UK, Canada, Australia), boards want one thing: provable ROI from security investments. That ROI shows up as fewer breaches, faster sales due to trust signals, smoother audits, and reduced insurance premiums.
Here’s the hook: InfoSec and Cybersecurity are not rivals—they’re layers of the same defense. InfoSec sets the governance, policies, risk appetite, and culture for all information (paper, people, processes, and digital).
Cybersecurity is the technical execution that protects digital systems, networks, and applications from live adversaries. When you align the two, your outcomes compound: improved conversion rates (security reviews pass faster), shorter time-to-market (compliance “green lights” instead of red flags), and lower cost of operations (automations, fewer incidents, tighter vendor controls).
In this guide, you’ll get practical comparisons, short case studies, and tidy tables you can share with executives and teams. You’ll also find career pathways and salary dynamics in 2025 language—what hiring managers actually look for, how degrees vs bootcamps compare, and how to move from Tier-1 roles into high-impact specialties (cloud, identity, DFIR, AppSec).
By the end, you’ll know where each discipline begins and overlaps, which roles fit your background, and how to sequence investments so your company (or career) captures maximum security ROI—and avoids headline risk.
Introduction to Types of Cybersecurity: Enterprise Challenges and ROI for Global Decision-Makers
Modern enterprises face three persistent challenges: attack surface sprawl, compliance obligations, and talent scarcity. Cloud, SaaS, and remote work expand the perimeter. Regulators increase expectations (ISO 27001, SOC 2, NIST CSF/800-53, PCI DSS, HIPAA, GDPR, Privacy Act AU, PIPEDA CA). Meanwhile, security teams compete for scarce skills.
Types of Cybersecurity most enterprises implement:
- Network Security: Firewalls, segmentation, NDR/MDR.
- Endpoint Security: EDR/XDR, device hardening, MDM.
- Application Security (AppSec): SAST/DAST, threat modeling, SBOMs.
- Cloud Security: CSPM, CIEM, CWPP, shift-left IaC scanning.
- Identity & Access Management (IAM): SSO, MFA, PAM, JIT access.
- Data Security: DLP, encryption, tokenization, data discovery/classification.
- Security Operations (SecOps): SIEM, SOAR, threat intel, incident response.
- Governance, Risk & Compliance (GRC): Policies, risk registers, audits, vendor management.
| ROI Lever | Measure | Typical Result |
| Fewer Incidents | MTTR, incident count | Lower downtime, lower insurance |
| Faster Deals | Security questionnaire SLA | Higher win rate, shorter sales cycle |
| Audit Readiness | Evidence coverage | Less rework, fewer penalties |
| Lower Cost | Tool consolidation, automation | Reduced vendor spend, FTE hours saved |
Mini case study (UK SaaS): A B2B platform struggled with enterprise sales due to “security questionnaires.” They aligned AppSec (secure SDLC) with GRC (evidence library). Result: security-review cycle dropped from 6 weeks to <2 weeks, raising close rates and ARR.
What is Information Security? Building Trust and Compliance for Tier One Enterprises
Information Security governs how information—any format—is identified, classified, handled, stored, shared, and destroyed. It establishes the risk appetite, the policies, and the control framework that Cybersecurity implements technically.
Core InfoSec functions:
- Governance: Policy library, standards, procedures, exceptions.
- Risk Management: Registers, likelihood/impact scoring, treatment plans.
- Compliance: ISO 27001, SOC 2, SOX, HIPAA, PCI DSS, GDPR/PIPEDA/Privacy Act (AU).
- Vendor Risk Management: Due diligence, DPAs, contract clauses, continuous monitoring.
- Awareness & Culture: Phishing simulations, role-based training, executive drills.
- Data Lifecycle: Classification, retention, legal holds, secure disposal.
Mini case study (Canada healthtech): A startup failed a hospital security review due to weak vendor risk controls. After implementing a supplier security policy, standardized questionnaires, and risk tiering, they passed procurement and closed a multi-year deal.
InfoSec ROI Table
| Area | Business Impact | How to Prove ROI |
| Policy & Governance | Reduces ambiguity, faster decisions | Fewer exceptions, audit success rate |
| Risk Management | Prioritizes spend on high-impact risks | Risk reduction over time, KRIs |
| Vendor Risk | Unlocks enterprise customers | Time-to-approve vendors, fewer incidents from third parties |
| Culture & Training | Fewer human-initiated incidents | Phish click-rate trend, report-rate trend |
What is Cybersecurity? Protecting Digital Assets for Growth and Lead Generation
Cybersecurity defends digital assets and services—networks, endpoints, apps, identities, data, and cloud—from adversaries. It’s the operational muscle that enforces InfoSec intent.
Key functions:
- Prevent: Hardening, least privilege, segmentation, WAF, MFA.
- Detect: SIEM/XDR rules, NDR analytics, behavioral baselines.
- Respond: Playbooks, SOAR automations, incident comms, forensics.
- Recover: Backups, DR/BCP tests, post-incident reviews.
Mini case study (Australia fintech): After a credential-stuffing wave, the team deployed risk-based authentication and bot defense. Login abuse dropped, legitimate user friction stayed low, conversion stabilized, and support tickets fell.
Cyber ROI Table
| Control | Business Metric | Outcome |
| MFA + SSO | Helpdesk resets, fraud rate | Lower support cost, fraud loss down |
| EDR/XDR | MTTR, lateral movement | Faster containment, smaller blast radius |
| CSPM/CIEM | Misconfig count | Fewer exposed services, audit wins |
| AppSec in CI/CD | Defect escape rate | Fewer hotfixes, faster releases |
Comparing Cybersecurity and Information Security: Which Delivers More ROI for Businesses?
Short answer: You need both. InfoSec sets direction and accountability; Cybersecurity executes technical defense. ROI peaks when leadership treats them as one operating model.
| Dimension | Information Security | Cybersecurity |
| Scope | All information (physical & digital) | Digital systems and data |
| Owner | CISO/CRO/Compliance leadership | SecOps/AppSec/CloudSec leads |
| Outputs | Policies, risk decisions, audits | Controls, detections, response |
| Success Metric | Audit readiness, risk posture | MTTR, incident reduction, uptime |
| Primary Enablers | Governance, risk, culture | Automation, analytics, engineering |
The CIA Triad: Core Enterprise Strategy for ROI and Trust in Security
Mini case study (US enterprise): Tool sprawl drove cost without risk reduction. A unified control catalog mapped InfoSec requirements to Cyber controls, removing overlaps. Outcome: tool consolidation, tighter detections, and clearer evidence for auditors and customers.
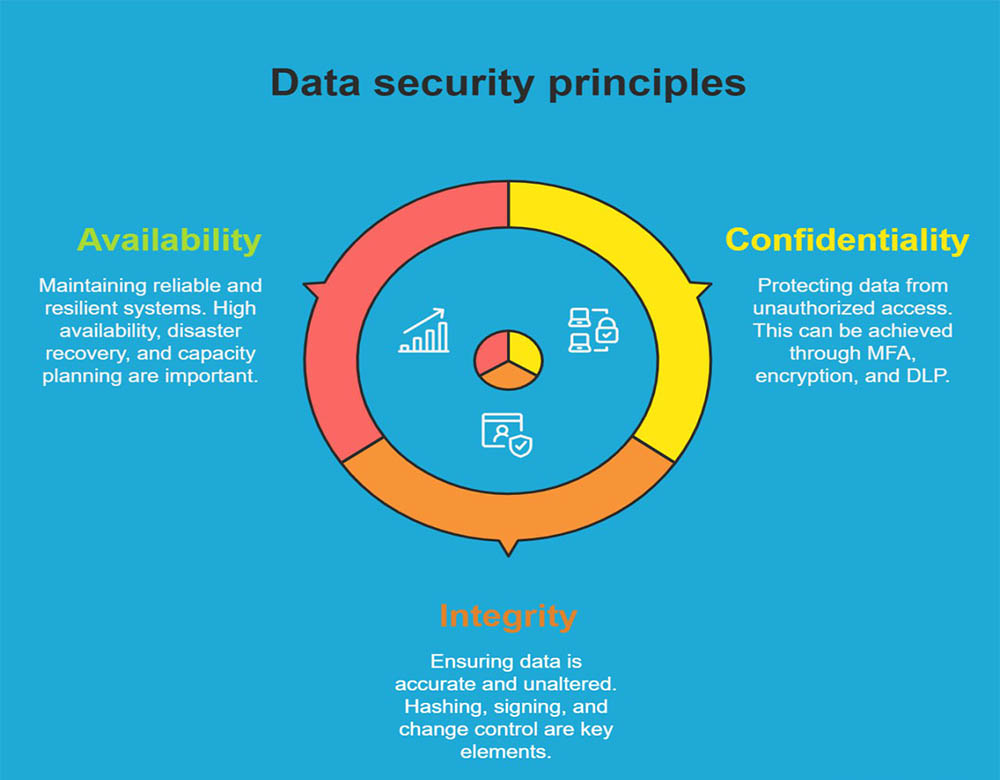
Confidentiality, Integrity, Availability (CIA) is the shared blueprint for InfoSec and Cyber.
- Confidentiality protects data from unauthorized access (MFA, encryption, DLP).
- Integrity ensures data is accurate and unaltered (hashing, signing, change control).
- Availability keeps systems reliable and resilient (HA, DR, capacity).
Pros/Cons Snapshot
| Pillar | Biggest Win | Common Pitfall |
| Confidentiality | Prevents data exfil/fines | Over-restricting access hurts productivity |
| Integrity | Trustworthy records & analytics | Weak change control = silent corruption |
| Availability | Revenue continuity | Over-engineering without BIA = waste |
Expert insight: Mature orgs tie CIA to business impact analyses (BIA). That converts abstract controls into clear SLAs executives can fund.
Primary Focus Areas: How Information Security vs Cybersecurity Impacts Enterprise Growth
InfoSec focus areas: Governance, risk quantification, third-party risk, culture, data lifecycle.
Cyber focus areas: Identity, endpoint, network, cloud, app, data, SecOps.
Growth impact:
| Function | Revenue Impact | Cost Impact |
| Vendor Risk (InfoSec) | Unlocks enterprise deals | Fewer vendor incidents |
| AppSec (Cyber) | Faster releases, fewer blockers | Less rework, fewer hotfixes |
| Identity (Cyber) | Lower fraud, less friction | Fewer support tickets |
| Training (InfoSec) | Fewer social engineering wins | Lower incident response hours |
Security Methods that Drive Conversion and Customer Trust in Tier One Markets
Security can increase conversion when buyers see proof:
- Public security page: Certifications, controls, incident process.
- Customer Evidence Folder: Pentest summary, policy list, data flow diagram, high-level architecture.
- Attestation cadence: Annual SOC 2/ISO audits, quarterly penetration tests.
- Runtime safeguards: MFA enforcement, SSO, RBAC, encryption at rest/in transit.
| Method | Signal to Buyer | Conversion Effect |
| SOC 2 / ISO 27001 | Independent assurance | Fewer objections |
| Detailed DPA | Legal & privacy maturity | Faster legal cycles |
| AppSec SDLC proof | Secure by design | Higher trust in roadmap |
| Incident playbook | Preparedness | Confidence under scrutiny |
Overlap Between Information Security and Cybersecurity: Enterprise Guide for ROI Optimization
Overlap areas include data classification, access control, incident management, and metrics. Use the overlap to simplify:
| Overlap | Joint Deliverable | ROI Boost |
| Data Classification | Uniform labels & handling | Easier DLP & rightsizing encryption |
| Access Control | Policy + IAM enforcement | Fewer exceptions, faster audits |
| Incident Mgmt | Policy + IR playbooks | Faster MTTR, less chaos |
| Metrics | Risk + Ops dashboards | Executive clarity → better funding decisions |
Expert insight: Build a single control matrix: column A = InfoSec requirement; column B = Cyber control; column C = evidence source. Audits and customer reviews get dramatically easier.
Confidentiality in Information Security vs Cybersecurity: A Step-by-Step Enterprise Checklist
- Classify data (public/internal/confidential/restricted).
- Map storage & flows (SaaS, databases, backups).
- Set access policy (least privilege, RBAC/ABAC).
- Enforce IAM (SSO, MFA, device posture, PAM).
- Encrypt data in transit and at rest.
- Monitor for exfil (DLP, anomaly detection).
- Review & recertify access quarterly.
- Test via red teaming and data loss drills.
Integrity: Why It Matters for Enterprise ROI and Data Protection in Tier One Countries
Integrity guarantees trustworthy data for decisions, billing, and audits.
- Controls: Hashing/signing, change management, code reviews, immutability for logs/backups.
- Process: Segregation of duties, release approvals, rollback plans, tamper-evident logs.
- Testing: DR/BCP with integrity checks, synthetic transactions.
Checklist ROI: Fewer finance disputes, cleaner audits, reduced fraud opportunities.
Availability: Ensuring Business Continuity and Growth Through Cybersecurity Services
Availability maintains revenue continuity and customer trust.
- Architect: HA pairs, multi-AZ/region design, capacity planning.
- Protect: WAF, rate limits, DDoS protection, circuit breakers.
- Recover: RPO/RTO targets, immutable backups, regular restore tests.
- Measure: Uptime SLOs, error budgets, incident comms playbooks.
Scope and Focus: What Decision-Makers in the USA, UK, Canada, and Australia Need to Know
- USA: Strong buyer demand for SOC 2, HIPAA, PCI; carrier requirements shaping control baselines.
- UK: ISO 27001 and GDPR rigor; NCSC guidance widely referenced.
- Canada: PIPEDA and provincial rules; healthcare and fintech scrutiny rising.
- Australia: Privacy Act & critical infrastructure focus; uplift on incident reporting.
Cybersecurity Degree Guide: Types, Specializations, and Career Paths in the USA and UK
- Degrees: BS/MS in Cybersecurity, Information Assurance, or Computer Science with a security track.
- Specializations: Cloud Security, Identity, DFIR, AppSec, GRC, OT/ICS.
- Early Roles: SOC analyst, risk analyst, junior AppSec engineer, IAM analyst.
- Growth Paths: Security engineer → architect; Risk analyst → GRC lead; DFIR → threat hunt/forensics lead.
| Path | Strength | Who Thrives |
| Engineering (AppSec/Cloud) | Hands-on building | Dev/automation-minded |
| GRC/Risk | Communication, frameworks | Policy/storytelling-minded |
| DFIR/Threat Hunt | Investigative | Curious, pattern seekers |
How to Get a Job in Cybersecurity: Requirements and ROI-Driven Career Insights
- Portfolio > buzzwords: Show labs, code, detections, threat hunts.
- Certs (role-based): Security+ (foundation), AZ-500/SC-100, AWS Security, GIAC, CISSP/CISM (later).
- Network: Local meetups, CTFs, open-source contributions, short write-ups.
| Quick Wins | Why It Works |
| Build a homelab + document | Proof you can operate controls |
| Contribute to a rules repo | Shows detection/automation skill |
| Redo CV around outcomes | Recruiters spot real impact fast |
Cybersecurity Bootcamp: What Enterprises and Students in Canada Need to Know in 2025
Bootcamps help career-changers demonstrate hands-on capability quickly. Look for:
- Employer input on curriculum, real tools (SIEM, EDR, cloud).
- Capstone tied to outcomes (detections created, IaC policy, threat model).
- Career support (mock interviews, portfolio reviews, hiring partners).
| Evaluate This | What “Good” Looks Like |
| Labs & Cloud Time | Dedicated hours, real consoles |
| Instructor Depth | Active practitioners |
| Placement | Transparent stats, alumni access |
Read More: Industry Reports and Insights on Information Security vs Cybersecurity Trends
- Frameworks: NIST CSF, ISO 27001 Annex A, CIS Controls.
- Buyer Guidance: NCSC (UK), CISA (US), ASD Essential Eight (AU), CCCS (CA).
- Market Signals: Insurance minimums, vendor risk questionnaires, privacy regulator updates.
Which is Better: Cybersecurity or Information Security? Expert ROI Insights for Enterprises
Best answer: whichever closes your largest risk gap first. If audits and customers stall sales, lead with InfoSec/GRC. If active threats or outages dominate, invest in Cyber/Engineering. Most organizations need a balanced roadmap within 1–2 quarters.
Are Cybersecurity and Data Security the Same? Analyst Perspective from Tier One Regions
No. Data Security is a domain (classification, encryption, tokenization, DLP). Cybersecurity covers broader digital defenses (identity, network, endpoints, apps, cloud) that enable data security to work at scale.
Is Cybersecurity Under Information Security? Enterprise Insights for Compliance Growth
Common model: Cybersecurity is a subset of InfoSec (which includes policy, risk, privacy, physical security). Some orgs invert the chart, but governance sits above engineering either way.
Which Pays More: Cybersecurity or Information Security? Salary Insights in the USA, UK, and Canada
Comp varies by role and seniority. Engineering-heavy roles (CloudSec, AppSec, DFIR, Red Team, Security Architecture) often command higher ceilings than generalist analyst/GRC roles; managers and leaders in either track out-earn most individual contributors. Location, industry, and scope drive deltas.
FAQs:
Information Security vs Cybersecurity Salary: Which Career Pays More in the USA and UK?
It depends on role depth. In general, technical specialties (cloud security, AppSec, DFIR, security architecture) often out-earn broad analyst roles. In the UK, ISO/GDPR-savvy GRC leads can match engineering salaries at senior levels. Key Tip: pick a track where you can demonstrate rare, revenue-relevant impact (e.g., enabling enterprise audits or stopping fraud at scale).
What are the key differences between Information Security and Cybersecurity (with examples)?
InfoSec governs how all information is protected—policies, risk, vendor controls, culture. Example: establishing a data classification standard and vendor DPA terms. Cybersecurity implements technical controls—identity, network, endpoint, cloud, app. Example: deploying MFA, EDR, WAF, and CI/CD scanning to block attacks.
Information Security vs Cybersecurity PDF Guide: Where to Download for Enterprise Training?
Create a lightweight internal PDF by exporting your security policy overview, control matrix (NIST/ISO mapping), and IR playbook. Include a one-page table from this article: scope, owners, metrics, evidence sources. Share via your Trust Center.
What is the difference between Information Security and Cybersecurity in tabular form?
Use this quick table:
| Item | Information Security | Cybersecurity |
| Scope | All information | Digital assets |
| Owner | GRC/Compliance/CISO | SecOps/AppSec/CloudSec |
| Output | Policies, risk, audits | Controls, detections, IR |
| Success | Audit pass, risk trend | MTTR, uptime, incidents |
Information Security vs Cybersecurity Reddit Discussions: What Experts in Tier One Countries Say
Common themes: frameworks vs pragmatism, certs vs portfolio, and “it depends” on org size. Practitioners stress hands-on skill, clear evidence for audits, and business-first communication.
What is an Information Security Analyst? Career Growth, ROI, and Salary in the USA and Canada
An InfoSec Analyst maintains policies, risk registers, awareness, vendor assessments, and control evidence. Growth paths: GRC lead, risk manager, compliance architect. Show ROI by reducing audit friction and accelerating enterprise deals.
Information Security Salary vs Cybersecurity Salary: Which Offers Better ROI in 2025?
Early-career pay may be similar; mid- to senior-level technical roles often rise faster. Leaders (CISO, Director, Head of Security) in either track command the highest comp. ROI improves when your work unlocks revenue and reduces measurable risk.
What are real-world examples of Information Security vs Cybersecurity in enterprises?
InfoSec: launches a third-party risk program, updates retention policy, runs privacy impact assessments. Cybersecurity: implements SSO/MFA, automates EDR quarantines, deploys CSPM to kill risky cloud misconfigs.
Information Security vs Network Security: Key Differences for Tier One Decision-Makers
Network Security is a subset of Cybersecurity focused on segmentation, firewalls, NDR, and traffic analytics. InfoSec is broader governance across all information. Use all three: InfoSec (policy) → Cyber (program) → Network (domain execution).
What is the cost of Information Security vs Cybersecurity services for enterprises in the USA, UK, Canada, and Australia?
Costs vary by size and criticality. Expect line items for audits/certifications, tooling (SIEM/XDR/CSPM/IAM), MDR/SOC services, and consulting for policy and architecture. Savings come from tool consolidation, managed services, and automation.
How do Information Security and Cybersecurity work together to ensure compliance and ROI?
InfoSec defines what “good” looks like (policies, control objectives). Cybersecurity implements how it runs (tooling, detections, response). Shared metrics and evidence close the loop—faster audits, fewer incidents, clearer executive reporting.
Which field offers the best jobs: Cybersecurity or Information Security in 2025?
Both offer strong demand. If you love engineering and automation, lean Cybersecurity (AppSec, CloudSec, DFIR). If you excel at frameworks and stakeholder alignment, lean InfoSec (GRC, privacy, vendor risk). The best jobs are those that tie security outcomes to business results.